Discovered a supply chain data breach a week before the public announcement
Able to monitor hundreds of suppliers for breaches
Detected a critical vulnerability within 2 hours of its release and patched it immediately
This Feedly for Cybersecurity client has graciously allowed us to share their story on the condition of anonymity. Client names have been changed.
THE CUSTOMER
This energy provider “helps keep the lights on for customers”
Started using Feedly Cybersecurity: 2020
This Feedly client plays a critical role across the Australian energy sector. In tandem with other market players, they help protect Australia’s national energy supply from cyber attacks. “We help keep the lights on for customers,” says Joe, Cybersecurity Threat Analyst.
THE CHALLENGE
Cybersecurity threat intelligence at human speed is no longer sustainable
The onslaught of information
The world of cyber threat tracking runs on a different clock than human speed. The firehose of cyber news makes it hard for our client’s security analysts to find the signal through the noise. Analysts like Joe and his team struggled to keep up with the onslaught of information. Joe used to manage his own personal spreadsheet of 350 sources of information, which he ranked by tiers based on how trusted they were. But the amount of screen time required to keep up with incoming information and identify trends was unsustainable. “The cyber world is like drinking from a firehose in terms of the information we see,” says Joe.
“There’s this concept of cyber time. Last week’s issue is like three years ago. We’re so swamped with information, we don’t have time to dive deep on a lot of stuff.”
Ever-changing types of attacks and attackers
As cyber threats and ransomware crews become increasingly sophisticated, the human ability to monitor the cyber threat landscape falls behind. No matter how knowledgeable you are, cybersecurity at human speed can’t keep up with ransomware crews using increasingly complex software to manage their operations.
For companies like this energy provider, the stakes are high. “If they encrypt our environment, we can’t supply energy to customers,” says Joe.
A data breach of even the smallest of our client’s vendors could put them at risk, so Joe and his team needed a way to keep an eye on even the smallest of breaches.
THE SOLUTION
Using AI to flag specific cyber attacks, threats, and vulnerabilities
The analyst team at this company needed better tools to help leverage their time and attention and stop doing manual research. Joe’s team had been using Feedly to aggregate information for years. But when his boss, Oliver, Cyber Security Manager, found out that Feedly’s cybersecurity-specific plan could use AI to flag cyber attacks, threats, and vulnerabilities, they knew they had to try it.
Organizing their security sources into focused Feeds
Oliver created Feeds around three main focus areas: renewable energy sources + cybersecurity, critical vulnerabilities, and supply chain threats.
The team selected sources of information they trusted to track cybersecurity news. Not all articles from their trusted sources concern the energy sector. To filter out cybersecurity news unrelated to the energy sector, they configured Feedly AI to flag articles about the specific areas they care about.
“Before using Feedly AI, we had very generic Feeds. We were just looking for energy and cybersecurity news in our region. But over time, I’ve been able to nuance our requirements over supply chain attacks, like Solar Winds.”
Tracking ransomware in the energy space
For example, the analyst team has always tracked news at the intersection of cybersecurity and the energy sector. But once they started using Feedly for Cybersecurity, they created an AI Feed to flag articles that cover ransomware in the energy industry.

Tracking supply chain attacks
“We were concerned about the supply chain risk for our company,” says Joe. “We talked to our internal procurement team to really understand our top 30 providers, with whom we spend millions of dollars.”
To track supply chain risks, the team selected the exact vendors they work with and created a personalized stream of intelligence to track risks coming from their supply chain. “We were able to turn the list of our top partners into an AI Feed and ask him to flag cyber attacks targeting those partners,” explains Joe.
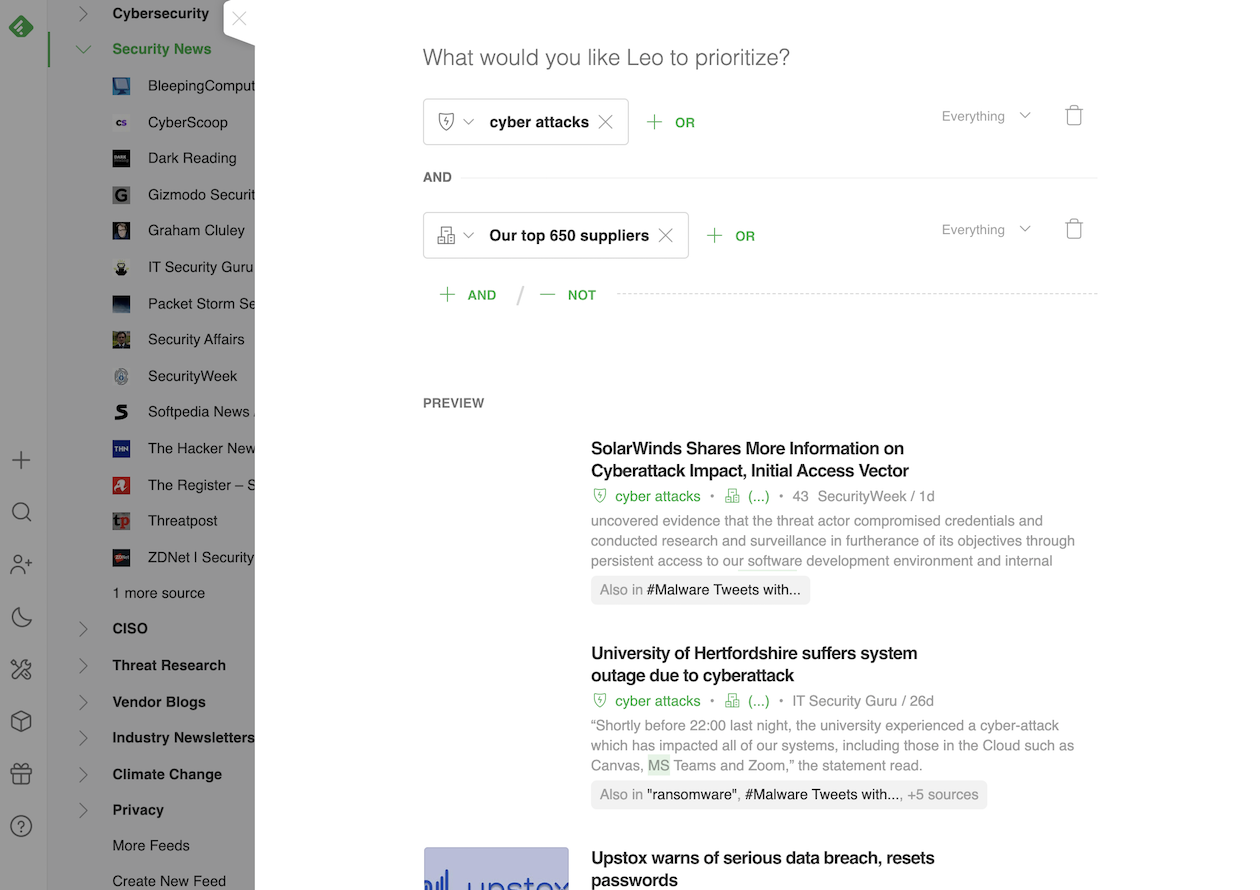
With an AI Feed n place, Feedly AI flags articles about data breaches related to any of the company’s suppliers, so they’ll know when one of the companies in their supply chain is breached or attacked. Feedly AI recognizes most of these names as companies, so he can differentiate if an attack is about Amazon (company) vs. Amazon (the river), for example.
Pushing articles to Slack to share with the local intelligence community
Beyond their internal intelligence team, Joe and Oliver share information across several platforms with peer organizations cybersecurity teams around the globe.
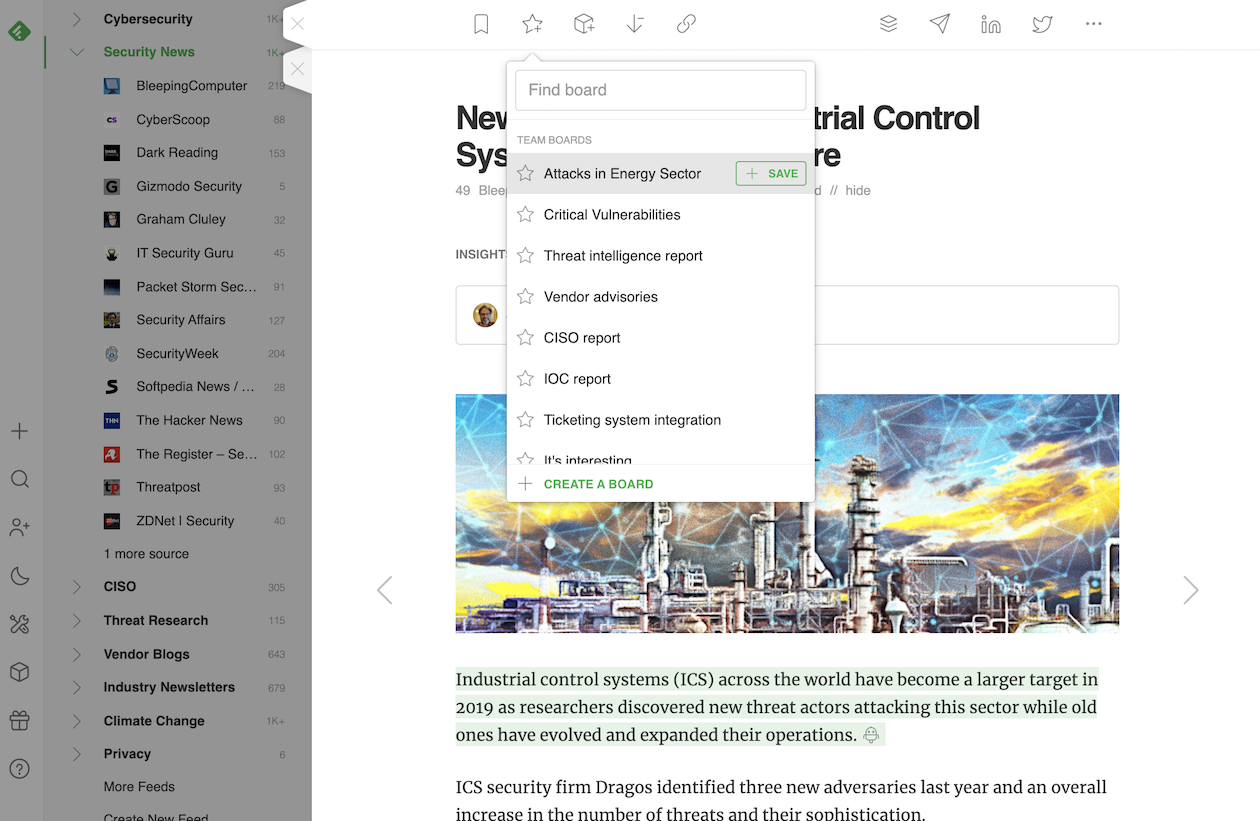
Joe and Oliver add critical articles to a specific Feedly Board. They’ve connected the Board to the collaboration platforms, so when Joe or his teammates add articles to the Board, their security community will automatically see critical updates.
THE RESULTS
Staying ahead of the curve
In October 2020, thanks to the work Joe had done to create AI Feeds based on their top 30 suppliers, his team proactively identified a data breach from one of their vendors.
“Thanks to my supply chain AI Feed in Feedly, we identified that one of our vendors had been breached a week before the company actually officially told us.”
This proactive alerting allowed Joe’s team to inform procurement areas and monitor leak sites to see if any sensitive material had been published. Luckily none had been released, and the issue eventually went away.
In March 2021, Joe checked his Feedly in the morning as usual, and found an F5 breach within two hours of the breach itself. “I was sitting at my desk, and I saw the F5 vulnerability pop up in Feedly. I pushed it out to management, and then there was a massive effort to patch that problem within two days, which was awesome.”
“I was sitting at my desk, and I saw the F5 vulnerability pop up in Feedly. I pushed it out to management, and then there was a massive effort to patch that problem within two days, which was awesome.”
Avoiding information overload
When a vulnerability is exposed, “information overload goes up — you can see how the malware reporting goes up associated with that particular vulnerability” says Joe. In response to an exposed vulnerability, there’s a corresponding increase in exploits. That’s where Feedly comes in. Instead of wading through pages of articles about vulnerabilities and exploits that don’t concern his company, Joe can use Feedly AI to surface vulnerabilities and exploits relevant to them.
“And that’s the power of Feedly. Using the smarts, intelligence, and Feedly AI’s natural language processing to align vulnerabilities with exploits. What pops out at the end is what you need to know, what you need to take action on. Not the noise.”
What’s next: expanding the supply chain tracking
In late 2020, the analyst team discovered that a smaller supplier was attacked after using a tool with an unpatched vulnerability. Criminals were able to steal data through a File Transfer tool. Our client was spending a relatively small amount of money with this company, so they weren’t on their list of top 30 suppliers, but this made Joe and his team realize they needed to expand their supply chain tracking in Feedly.
The more they personalize their Feeds with help from Feedly AI, the more our client’s security analysts can stay focused on the real threats. As Joe trusts Feedly more and more, he can focus on the high level analysis, and rely on Feedly AI ‘s natural language processing to do the tedious work for him.
Joe is excited for the possibilities to get even more proactive with upcoming Feedly features. In addition to their supply chain tracking project, the analyst team plans to use the Feedly API to push alerts directly to their internal intelligence platform, which will make it even easier to focus on threats.
From a proactive monitoring perspective, the power of using Feedly is to actually inform you of breaches before anyone else knows.”
More proactive threat intelligence. Less noise.
Streamline your threat intelligence in Feedly so you can focus on real threats and ignore the distractions.